Page 201 - 1-37
P. 201
TRANSFORMING TRANSFORMING TRANSFORMING
SUSTAINABILITY REPORT FY 2023 COMMUNITIES THE PLANET THE WORKPLACE
Information Security Policies and
Certifications
We have established an information security a) Internal Vulnerability Assessment and
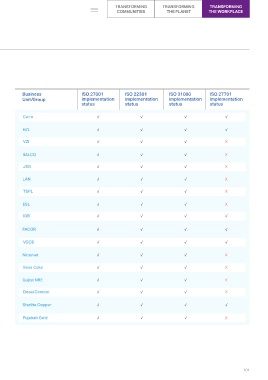
policy and data governance policy, covering Penetrating Testing (VAPT) Program Business ISO 27001 ISO 22301 ISO 31000 ISO 27701
implementation
implementation
implementation
implementation
Unit/Group
aspects such as information security, risk undertaken by BU Information Security status status status status
management, disaster recovery, business Function (Through Third-Party Expert
continuity management, and data privacy. Agency) Cairn √ √ √ √
These policies form an integral component
of Vedanta's Information Security framework, b) External Vulnerability Assessment and HZL √ √ √ √
showcasing the Company’s dedication to Penetrating Testing (VAPT) Assessment
robust management practices. Business through Group Management Assurance VZI √ √ √ X
continuity/contingency plans and incident System (Through Third-Party Expert
response procedures are in place that are Agency) BALCO √ √ √ X
tested bi-annually. Regular trainings for our c) Red Teaming Exercise as part of point # 2
employees on cybersecurity are conducted. JSG √ √ √ X
d) Surveillance Audit under ISO 27001, ISO
22301, ISO 31000, and ISO 27701 LAN √ √ √ X
Framework Requirements (Through
Policies defined by Vedanta are categorised under
the following areas: Surveillance Audit Partner) TSPL √ √ √ X
• Information Security e) Assessment of IT General Controls (ITGC) ESL √ √ √ X
Management Policies by Statutory Auditor under
Sarbanes-Oxley (SOX) Compliance IOB √ √ √ √
• Data Governance & Privacy Framework (Through Statutory Auditor)
Policies
FACOR √ √ √ √
• Risk Management Policies
These vulnerability assessments, including
• Business Continuity Management simulated hacker attacks are carried out on VGCB √ √ √ √
Policies an annual basis by globally reputed and Nicomet √ √ √ X
• Incident Response & Emergency recognised third-party agencies, including a
Preparedness Plan team of certified and qualified personnel in Sesa Coke √ √ √ X
various domains of cyber security and data
governance. Gujrat NRE √ √ √ X
Vulnerability Assessment
BUs have obtained ISO certifications and are Desai Cement √ √ √ X
Vulnerability identification, monitoring and committed to establishing, implementing,
tracking of mitigation actions and continuous maintaining, and continuously improving their Sterlite Copper √ √ √ √
compliance level are being done through Integrated Management System (IMS) in
various assessments. Vedanta carries out alignment with the standards set forth by ISO Fujairah Gold √ √ √ X
and undergoes the following assessments to 27001, ISO 27701, ISO 22301, and ISO
identify vulnerabilities, threats, 31000. 71.43 % of our IT infrastructure is
short-comings, and the associated certified as per ISO 27001
risk/impact:
101